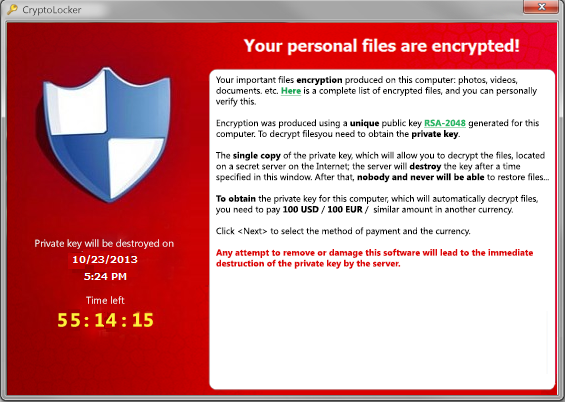
What Is CryptoLocker?
CryptoLocker is a one of a new breed of malware known as ransomware, that once it has infected a users computer restricts access in some way, and demands a ransom to restore access.
How serious is the infection?
In a word, VERY! Once you have become infected with CryptoLocker the only way to get your files back is to pay the ransom.
What does CryptoLocker do?
Basically once you have become infected with CryptoLocker, the malware will scan your files looking for documents, videos, pictures etc and will encrypt them in a fashion that is completely irreversible without the correct description program and decryption key, and the only way to obtain those is to pay the ransom.
How do you get infected with CryptoLocker?
The current method of CryptoLocker infection is by opening an executable file attachment that is received as part of an email scam. There are no other known methods at the time of writing.
Can I prevent a CryptoLocker infection?
As with all malware infections, prevention is definitely better than cure – Basic security measures such as not opening email attachments unless you know they are safe, making regular backups, keeping your Operating System up to date with the latest security patches, running up to date security software, and not visiting some of the more shady parts of the internet will all help in keeping you safe.
I have become infected, what can I do?
In a nutshell, nothing.
If you have lost files to CryptoLocker that are important and you don’t have a backup then your only option is to pay the ransom. Whilst this flies in the face of the normal advice for ransomware infections, it is your only option, and reports from those that have paid the ransom indicate that the files will be restored back to their original un-encrypted format. If you have adequate backups of the affected files all you need to do is use the removal tools available here, and then restore the files from your backup.
Is there anything I can do to avoid being infected by CryptoLocker?
Yes – if you take all the usual precautions to keep yourself safe, then you should be OK – CryptoLocker is currently being spread via a malicious email attachment, so not opening attachments is always a good idea. Undoubtedly someone will find another way to spread CryptoLocker in the future and appropriate precautions will need to be taken then. FoolishIT have created a free CryptoLocker prevention tool here that will help to protect you from infection in the future and looks like it’s being updated regularly to deal with different attack vectors. We recommend you download and use this tool on all Windows based computer you use immediately.
This post is a summary of the full CryptoLocker guide published by Bleeping Computer – for full information and recommended action and removal tools please see the original guide at http://www.bleepingcomputer.com/virus-removal/cryptolocker-ransomware-information