WARNING – Cracking WPA keys could get you into serious trouble! Only attempt this procedure on a network that you own, or have the network owners permission to try this on. Chimpytech.com cannot be held responsible for any illegal activity you may undertake in using these instructions.
Wi-Fi Security
Many people are under the mistaken belief that they are safe from intruders on there Wi-Fi network if they are using the WPA/WPA2 protection option on their router. Unfortunately, cracking WPA has become a little easier with the introduction of WPS. The router manufacturers have inadvertently undermined this security when they came up with the idea of WPS (Wi-Fi Protected Set-up) which was meant as a way of making the entry of a long Wi-Fi password much easier. (Click Here for the Wikipaedia entry for WPS)
If you have a router and are using WPA/WPA2 then you may well be vulnerable to having your password revealed using an easily obtained tool from the internet, and a little time on the part of the hacker trying to gain access – we will show you how to audit your router to see if you are vulnerable. (This procedure can also of course be used to attempt a break in to a router other than your own, please do not do this, cracking WPA is probably illegal in your country and is generally a bad think to do – read the warning at the top of the page!)
For this article you will need:
- A computer or laptop that is wireless enabled, and not currently connected to the router to be hacked.
- A copy of Kali Linux available via Offensive Security from www.kali.org
It is beyond the scope of this article to show you how to set-up and run Kali on your chosen machine, but there is plenty of good documentation and support available at the Kali website – we would recommend creating a ‘Live’ DVD and using that to experiment with.
Once you have got Kali downloaded, burnt to DVD, and have familiarised yourself with its interface, you can start to test the security of your router.
Find the information you need to start Reaver
- Open up a terminal Window and type: iwconfig
- You will see a list of network devices listed, and one will be your wireless card – it will probably be something like wlan0 or wlan1, but maybe be different depending on your exact network setup.
- Next we will need to put the card in to ‘Monitor Mode’ so assuming your card is wlan0 we now type the command airmon-ng start wlan0
- This will now set the card in to Monitor Mode, and tell you what the interface name is – usually this will be mon0, but it could be any number starting monX
- The last piece of information you will need is something known as the BSSID of the router you wish to audit, (The BSSID is basically a manufacturers serial number, and should be unique for every network device on the planet) to get this type the command airodump-ng mon0
- You will see a screen showing a list of all local wireless networks, when you see your router listed press ctrl+c to halt the scan. now that the scan is halted you need to copy down the BSSID of your router/network, it will look something like AA:E4:54:D2:6C:87:1A.
Starting up Reaver
- The specific tool within Kali to execute the attack is called ‘Reaver’ and is very easy to use once you have all the information collected above.
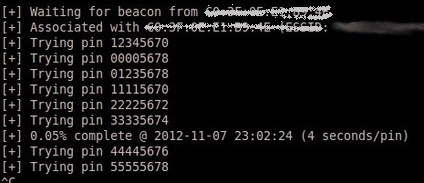
- In the Terminal Window type in the command reaver -i mon0 -b AA:E4:54:D2:6C:87:1A -v (You will of course need to change mon0 and the BSSID to the ones you obtained yourself) and hit enter, now watch as Reaver attempts to find your WPS PIN, and subsequently your routers pre-shared key.
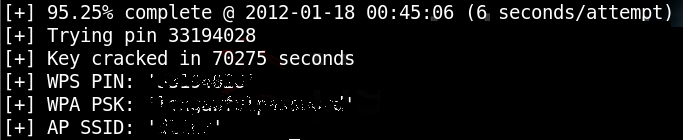
After what will probably be a few hours you will eventually see a screen like the one below, showing your WPS PIN, WPA Pre-Shared key, and your networks SSID name.
On older routers the key can usually be obtained in around 4-6hrs as there are no checks or controls in place to guard against a Reaver attack, so cracking WPA keys is relatively quick.
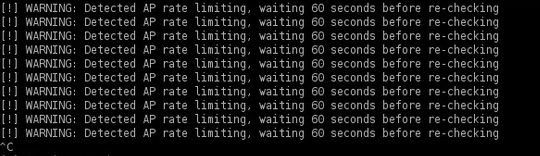
On newer routers you may well see a message saying that the router has timed out, and Reaver will try again in about 60 seconds. This is because the manufacturer has built protection in to the router that detects against a brute force attack, and only allows a certain amount of failed attempts before locking down the router for a period of time. This doesn’t mean the router is impervious to the attack, it just means that cracking WPS keys will take longer, given enough time Reaver will still find the PIN and Pre-Shared Key.
How Can I Guard Against This Attack.
The only way that you can guard against this attack is to completely disable the WPS option in your routers control panel, but be aware that some routers will still leave WPS on, even if you turn it off in the control panel, so we would recommend trying another round of cracking WPA with Reaver after switching it off just to be sure.